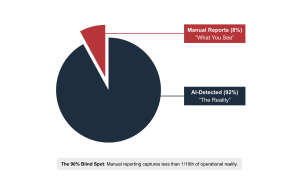
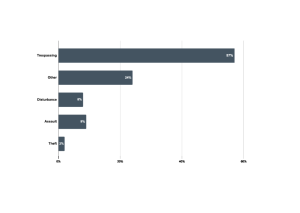
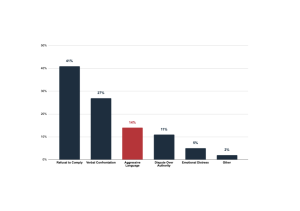
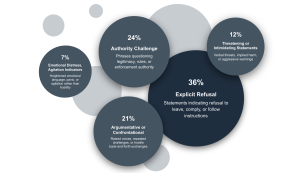
Improve Shift Management Operations with a Unified Approach
Gurmit Dhaliwal, Celayix, CALSAGA Associate Member
Security operations are becoming more complex, but the systems used to manage them haven’t kept pace.
Hiring, shift scheduling, time tracking, payroll, and billing are often handled in disconnected tools. Even so-called “all-in-one” platforms struggle to meet the needs of sophisticated security organizations, where requirements evolve constantly, and operational precision is non-negotiable.
Legacy software and broken workflows lead to miscommunication, staffing gaps, compliance risk, and lost revenue. As complexity increases, these failures become harder and more expensive to manage.
When Communication Breaks Down, Operations Suffer
For security operations to run smoothly, accurate data and timely communication must flow across every system.
New guards must be onboarded correctly and made available for shifts without delay. Scheduling must account for qualifications, availability, and location requirements to ensure the right guard is deployed at the right time. Shifts must be communicated clearly and accepted quickly, with transparency that reinforces fairness and trust.
When communication fails, the impact is immediate: no-shows, frustrated employees, higher turnover, and missed revenue. Inaccurate or delayed time and attendance data creates downstream payroll and billing issues, leading to reconciliation headaches, payment disputes, and compliance risks.
Small data failures quickly become operational chaos.
Why All-in-One Software Falls Short
Every function within a security operation has unique requirements.
HR teams need flexible hiring workflows. Schedulers need real-time visibility and intelligent tools to deploy the best available guard across multiple job sites. Finance teams require precise, compliant data flow between time tracking, payroll, and billing.
All-in-one systems promise simplicity but sacrifice depth. They are built for the average use case, not the operational realities of complex, growing security organizations. As a result, businesses outgrow them quickly—or never fully realize their potential.
Sophisticated operations require flexibility, specialization, and control.
The Power—and Challenge—of Best-of-Breed Solutions
Best-of-breed platforms excel by focusing deeply on a single domain. They deliver advanced functionality, industry expertise, and continuous innovation that generic systems can’t match.
The challenge has always been integration. Connecting specialized systems traditionally required custom development, ongoing maintenance, and internal technical resources that many organizations don’t have.
As a result, many security firms settle for suboptimal systems—not because they want to, but because integration felt too complex.
The Evolution to a Unified, Integrated Approach
That trade-off no longer exists.
Modern APIs and native, pre-built integrations now enable specialized platforms to work together as a cohesive system. Instead of stitching tools together manually, forward-thinking vendors are partnering to deliver seamless, production-ready integrations out of the box.
This unified approach allows each system to operate at its full strength while data flows automatically across the organization, from hiring to scheduling to payroll and billing.
The result:
- Fewer errors and less manual work
- Faster, more reliable staffing decisions
- Better employee communication and engagement
- Improved billable utilization and lower administrative costs
- Built-in compliance that adapts as requirements change
Better data flow enables smarter automation and clearer analytics, providing visibility into true shift costs and operational efficiency. Organizations gain the agility to adapt quickly, whether responding to client demands, workforce changes, or growth opportunities.
A Unified Workforce Without Compromise
Native, intelligent integrations create a unified workforce management ecosystem without sacrificing flexibility or control. Security organizations can mix and match best-of-breed tools while operating as a single, cohesive system.
The outcome is clear: fewer bottlenecks, less chaos, and a foundation built for scale.
As one Project Manager at Cerberus Security Group put it:
“The proof is in the pudding. Celayix and isolved have solved a lot of things overnight. The training was really amazing. It’s sophisticated software, but not complicated at all from a user standpoint.”
For security organizations ready to move beyond fragmented systems and outdated workflows, a unified approach delivers what all-in-one solutions never could: clarity, control, and confidence at scale.
For a real-world example, see the recent announcement on Celayix and isolved partnering to deliver unified workforce management for the security industry.
 Gurmit Dhaliwal is the CEO of Celayix, which delivers shift management for workforce operations and helps ensure every shift is covered. His 25 years of experience in employee scheduling and time-and-attendance software help improve shift management for the security guard industry. He understands the complex requirements of the industry, such as compliance with California State Laws and integrating best-of-breed tools to simplify workflows and accelerate operations.
Gurmit Dhaliwal is the CEO of Celayix, which delivers shift management for workforce operations and helps ensure every shift is covered. His 25 years of experience in employee scheduling and time-and-attendance software help improve shift management for the security guard industry. He understands the complex requirements of the industry, such as compliance with California State Laws and integrating best-of-breed tools to simplify workflows and accelerate operations.